It was a regular working day. I was shuttling between meetings with clients and meetings with my team. And one of my team members came to me suddenly and said our website is not working.
June 1st, to be precise. Our website was hacked. When I heard the words, I didn’t know it was going to be a month of embarrassment and loss. When I checked the website the previous day, it was there. And suddenly, it wasn’t.
We tried logging into our GoDaddy account but could not. It kept saying, “Password Invalid”! We tried resetting the password via the “Forgot Password?” option. We entered our details but the link to reset the password was being sent to a completely different address. It wasn’t mine!

Then began a series of phone calls. First, to GoDaddy’s Support Team in Hyderabad. And then to their team in the USA. A total of forty hours vanished while waiting for them to help with the password. But the worst was yet to unravel.
I still had no clue about the extent of the damage. At that moment, it only meant a few teasing messages from extremely close friends. That The Digital Fellow had disappeared.
The password had been changed. But there were many questions. Who changed it? (Clearly, it wasn’t me.) How? When?
June 3rd. We called up the support team at GoDaddy once again. It turns out they outsource their support-related work. So, every time we called, it was a different agent on the line. And we had to repeat the entire story each time. It was extremely frustrating.
Little did we know that the ordeal would go on for many more days.
The US support team asked us to send a request email to an email address. It seemed writing that one email would solve everything.
Had that happened, the blog would have ended right here.
We still hadn’t regained access to our account. Response to every email from GoDaddy takes 24 to 72 hours.
June 5th. They wrote back asking for additional documents. We sent them immediately and kept calling them as well to see if there were other alternatives to make this ordeal a little less painful.
June 6th. We received a reply. It simply said:
“The domain ownership update has expired.

This applies to the following domain(s):
thedigitalfellow.com
If you’d like to restart the process, the current domain registrant needs to request the change again.
If you have questions, please call us at 040 67607600.”
It was getting worse! All the document hunting for this? We called up the support team at GoDaddy once again and explained the whole scenario. They simply asked us to apply again at changeupdate.com. Meanwhile, we discovered that someone had hacked our account, changed the passwords, registered a different email address with GoDaddy, and enabled a two-step authentication too! So, even the support team at GoDaddy couldn’t get into the account!
June 9th. Another email. Again, as apathetic as it can ever get:
“Information regarding your request
Our support staff has responded to your request, details of which are described below:
Discussion Notes
Support Staff Response
It appears from the domain status that these domains were moved between accounts recently (after your request was made).
Please clarify if you have regained control of the domains or if you still want to process a claim. Thank you.
Thanks,
Customer Service”
The hacker had transferred the domain from our original account to another account. We wrote once again explaining everything! As we knew by then, we would have to wait for 24–72 hours for their reply.
But we kept calling. And explaining again and again — the previous emails, our invoices, and evidence from “WHO IS” look up.
Imagine their persistence too! All they always said was: to raise the issue at changeupdate.com and wait for a response!
June 12th. Another email. A ray of hope. But instead, it said:

Happy to help! Imagine the irony!
We had to call once again. The team at Hyderabad couldn’t do much. That meant calling the US team. And that meant sleepless nights because of the different time zones.
We were losing sleep not because of the calls alone. The website is the most important asset of any business. It was even more crucial for us because website development is among the bouquet of services we offer. How could someone working with digital media lose his website?
Our existing clients started asking about what had happened. The prospective clients started wondering if we were a fake company! There were a lot of followers and well-wishers who regularly consume content from our website. They started sending us screenshots of the status of our website.
The whole world was booing us!
This was no time to react though. We had only one goal. To get the website back. That equaled to: keep calling GoDaddy.
In one such telephonic conversation, their support team suggested that we should cancel the 2-step authentication on our account. That would let GoDaddy into the account and their team could then look into the matter.
June 13th. We wrote to them requesting them to cancel the 2-step authentication. We threw in all our documents, invoices, and “WHO IS” records to prove that we were the original account holders.
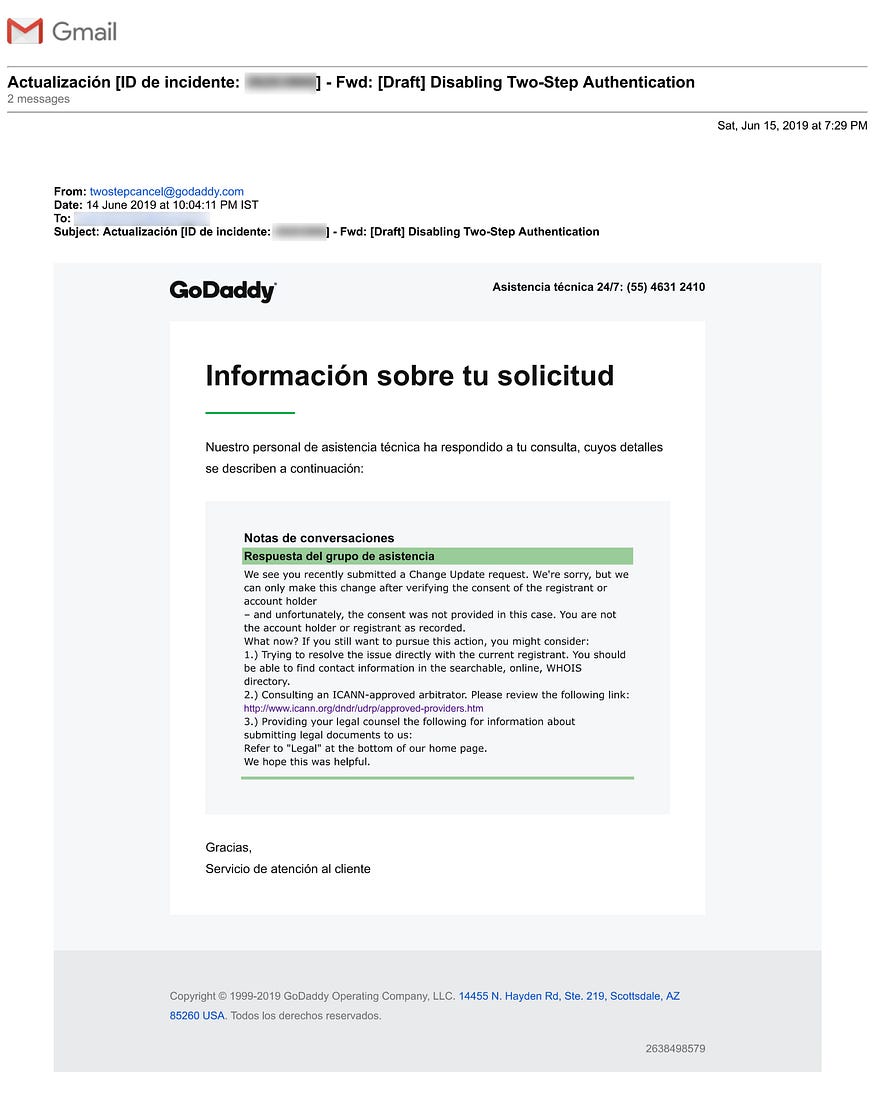
June 17th. We spotted the email. A terse email from GoDaddy. Request denied. Because we were no longer the owner. Courtesy: the hacker. Account settings changed. Domain ownership changed. The hacker had created another account with similar account details and transferred the domain to that account.
June 18th. We got back to their team at Hyderabad. We explained everything all over again. We also added that we hadn’t authorized any transfer of account. They tried very hard to blame it all on us. They kept saying that everything happened because the password of our registered email address had got compromised.
But we knew better. Cyber attacks can bypass emails. Breaking news, right? Especially to the ones who don’t think about websites getting hacked.
The team put our call on hold. When the agent got back, he admitted: yes, there are always such loopholes!
Yes, dear reader. A hacker can get into the domain account without using your email address. And then change all the information like the registered email address once inside.
They insisted that they wanted to speak to me, the account holder. I wasn’t around though because I was in a client meeting.
They then got in touch with the US team, explained the whole scenario to them, and registered a complaint in their Fraud Department. That was some action. Because all our efforts with the US team had never reached anywhere.
2 more days. Still waiting.
June 20th. An email from GoDaddy:
a. Here’s our response to your request.
Discussion Notes
Support Staff Response
We have reviewed and reverted your account. When you have the ability to log in to a computer, please contact our 24/7 Customer Support department for assistance with gaining access back to the account. They can be reached at 480.505.8877 or (https://www.godaddy.com/contact-us.aspx).
If you need any additional help, call us anytime at 040 67607600 and reference Incident
ID [Incident ID: 39265224].
b. Two-Step Verification has been disabled.
You recently removed Two-Step Verification from your account. This means a verification code isn’t required for someone to sign in.
You can turn 2-Step Verification back on at any time from the 2-Step Verification page in your account settings.
If you didn’t intentionally turn off 2-Step Verification, please access your account right away. Sign in and go to your Account Summary page to check that your contact information is correct and that nothing has been changed. If you notice any activity that you didn’t authorize, change your password and re-enable 2-Step Verification.
If you have questions about accessing your account, call our support team at 040 67607600.
June 21st. We called the US team and shared the email as per their instructions in the email.
Their first response was: Call in the evening! Because the 2-step authentication team works only in the evenings!
We were about to lose it when they asked us to hold on for a minute. When their agent came back on the line, he generously announced that the 2-step authentication had been removed. They verified our details, changed back the registered username, and sent us a password reset link.
We reset the password and enabled the 2-step authentication once again.
But that was not the end! We had merely gotten our GoDaddy account back. Not the domain. The domain still lay transferred to another account.
We had to shoot another email to request access to our domain. We promptly did so. But it was a Friday. We had to wait.
June 24th. No email. We called. The transfer was in progress. We had to wait some more.
June 25th. THE email. Domain Transfer successful. We had our account back.

25 days of struggle. Countless hours of national and international calls. Our story was repeated at least 50 times to different agents.
All to understand the silly loopholes in a system that handles and manages the websites of the world.
So, finally, there was a good ending to that story. All we know is that our invoices stood by us.
Maybe our service provider asked the hacker too and “he” couldn’t produce anything to show that he owned the account. We’ll never know.
Because the hacker isn’t easy to identify. The service provider gave us some details like his
virtual number. But that was a fake one. We couldn’t trace it to a person.
The hacker didn’t identify himself either. There wasn’t any demand for ransom. Not yet at least.
So we don’t know why he took all that trouble. Did he do it because it was easy to fool the service provider? Did he do it because he wanted to make some bucks out of us? Did he do it for our client's data? But then we don’t store any such data on our website.
Some things always stay mysteries.
But there’s a silver lining to this experience: a realization. That we’re getting noticed. For our work. For our content.
So here we are. We bounced back.
We finally have our website back. We’ve changed the image on our home page to something topical. We’ve added a whole new “DaysImportant” page. Did you take a look?
Your website is your most crucial digital asset. Your presence elsewhere like on different social media platforms is only intended to drive traffic to your website.
Have you thought about keeping your website secure? Which precautions have you been taking? Are you sure they’re enough?


